Copyright © 2025 KVMGalore® - All rights reserved.

AdderView Secure
Secure EAL4+ certified USB, dual-link DVI-I & audio KVM switches prevent outside emissions snooping and information flowing between computers
Read more below...

1) AdderView Secure Digital, 2-Ports Model No. AVSD1002-US  Ships in 7-10 business days or less
Ships in 7-10 business days or less

2) AdderView Secure Digital, 4-Ports Model No. AVSD1004-US  Ships in 7-10 business days or less
Ships in 7-10 business days or less
Ultra secure EAL4+ certified USB, dual-link DVI-I and audio KVM switch
ideal for government, military and other secure-data environments
AdderView secure KVM switch allows a keyboard, monitor and mouse to be shared between high and low security systems, sometimes known as red and black networks, and is designed carefully to prevent information flowing between computers or to the outside world via emissions snooping.
The AdderView secure design prevents sensitive data from leaking between ports, sensitive data leaking to the outside world and sensitive data from being stored in the device to actively combat a range of potential leakage "threats".
AdderView Secure Digital are highly robust KVMA switches for critical applications. When information absolutely must not be leaked between systems or networks, AdderView Secure units combine the necessary isolation with a desirable ease of use.
 AdderView Secure units combine a number of overlapping strategies that are designed and proven to defeat potential points of infiltration or protect against user error. Firstly, all channel switching is controlled only from the front panel buttons. No keyboard or mouse switching commands are permitted and all operations are continually monitored by a dedicated sub-system. Any deviation from a strictly ordered sequence of events will result in an error condition, where all channels are immediately isolated and the operator is informed via a front panel indicator.
AdderView Secure units combine a number of overlapping strategies that are designed and proven to defeat potential points of infiltration or protect against user error. Firstly, all channel switching is controlled only from the front panel buttons. No keyboard or mouse switching commands are permitted and all operations are continually monitored by a dedicated sub-system. Any deviation from a strictly ordered sequence of events will result in an error condition, where all channels are immediately isolated and the operator is informed via a front panel indicator.
 Data diodes, implemented within hardwired electronic circuitry, rather than software, are liberally employed to ensure that critical data paths can flow only in one direction. These data diodes ensure that a compromised peripheral, a keyboard for instance, cannot read information back from a connected system in order to transfer such details to another system. Whenever a channel is changed, the connected keyboard and mouse are always powered down and re-initialized to provide yet another level of protection against hidden peripheral malware.
Data diodes, implemented within hardwired electronic circuitry, rather than software, are liberally employed to ensure that critical data paths can flow only in one direction. These data diodes ensure that a compromised peripheral, a keyboard for instance, cannot read information back from a connected system in order to transfer such details to another system. Whenever a channel is changed, the connected keyboard and mouse are always powered down and re-initialized to provide yet another level of protection against hidden peripheral malware.
In general, the role of software within the unit has been reduced to an absolute minimum to avoid the possibility of subversive reprogramming. Additionally, all flash memory has been banished from the design, to be replaced by one-time programmable storage which cannot be altered.
The outer casing contains extensive shielding to considerably reduce electromagnetic emissions. Additionally, the casing has been designed with as few apertures as possible to reduce the possibility of external probing and several primary chassis screws are concealed by tamper-evident seals to indicate any unauthorized internal access. Shielding extends also to the internal circuitry with all channels providing a minimum of 60dB crosstalk separation between computer input signals and any signals from the other computers at frequencies up to 100MHz.
These are just a few of the many strategies and innovations that have been combined to ensure separation between differing systems. Numerous other defences lie in wait to defeat any potential threat.
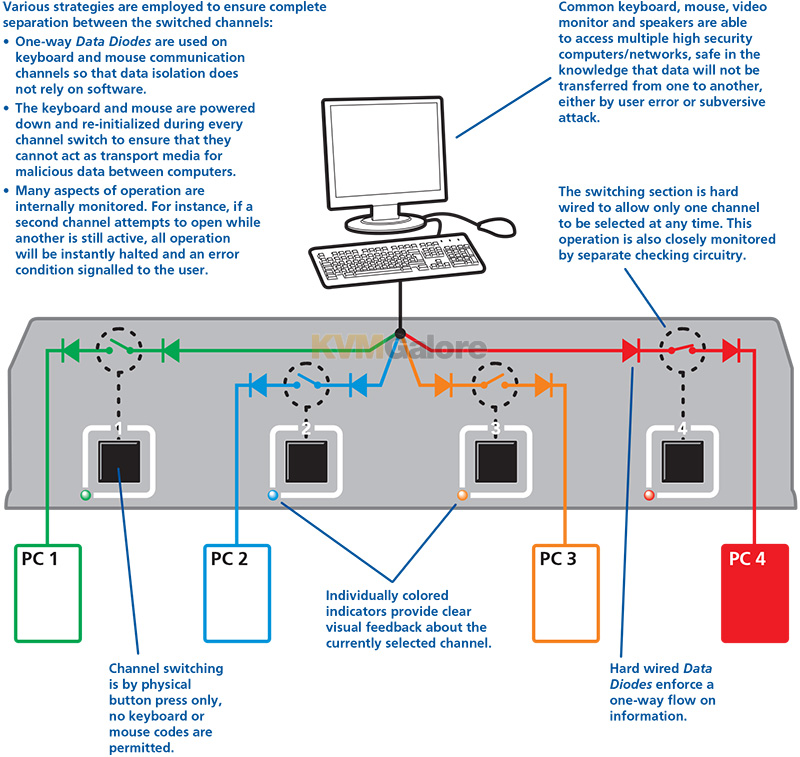
Various strategies are employed to ensure complete separation between the switched channels:
• One-way data diodes are used on keyboard and mouse communication channels so that data isolation does not rely on software.
• The keyboard and mouse are powered down and re-initialized during every channel switch to ensure that they cannot act as transport media for malicious data between computers.
• Many aspects of operation are internally monitored. For instance, if a second channel attempts to open while another is still active, all operation will be instantly halted and an error
condition signalled to the user.
More security features
• Common keyboard, mouse, video monitor and speakers are able to access multiple high security computers/networks, safe in the knowledge that data will not be transferred from one to another, either by user error or subversive attack.
• The switching section is hard wired to allow only one channel to be selected at any time. This operation is also closely monitored by separate checking circuitry.
• Channel switching is by physical button press only, no keyboard or mouse codes are permitted.
• Individually colored indicators provide clear visual feedback about the currently selected channel.
• Hard wired data diodes enforce a one-way flow on information.
• The casing is shielded to reduce electromagnetic emissions to an absolute minimum. Casing is secure with access apertures minimized and vital access screws having tamper-evident
seals.
• Switching is controlled solely by the clearly labeled front panel buttons. Each selected channel is represented by an individually colored indicator to provide additional visual feedback.
• Clear error indication. Any unexpected operation (such as an attempt to select two channels simultaneously) will be signalled by the ERR indicator, accompanied by complete isolation of all channels.
• Clear and simple connections. All connections are clearly marked to avoid any ambiguity. Full dual link DVI-I video connections are provided and USB connections are used throughout for keyboard and mouse links.
• Clear stored states. Attached keyboard and mouse are both powered down and reset at every switchover to clear stored states.
| Threat | Solution |
|
Data being sent to ports by means of faulty or subverted keyboards or mice causing the channel to switch and sending data in turn to each port |
Channel switching is controlled by the front panel buttons only with all keyboard hotkey or mouse switching capabilities removed from the design. |
| Data transfer by means of common storage | USB ports support keyboard and mouse connections only. The roduct does not enable a USB memory stick or disk drive to be shared between computers. Unidirectional keyboard and mouse data signalling protects against data transfer across the switch. |
| Timing analysis attacks | If a connection exists between a computer and a shared microprocessor system, it is potentially possible to determine what may be happening on the micro by timing the responses to repeated requests that the micro must service. For example, if a high data bit takes longer to transmit through the system than a low bit it may be possible to detect the pattern of data flowing between other ports by attempting to time the responses to otherwise normal requests. In the AdderView Secure, each port has a dedicated processor that only has input signals from the rest of the system. These input signals are only active when the port is selected. Consequently a timing analysis attack from one computer would yield no information about data flowing to another computer. |
| The user selects the wrong port | Only one simple method of selecting computers is provided. The selected port is clearly and unambiguously indicated on the front panel by means of colored lights adjacent to each key switch. For high levels of security, the screens of high and low security computers should be arranged to look visibly different in general appearance. |
| Forced malfunctions due to overloaded signalling | It is potentially possible to create forced malfunctions by constantly and quickly sending a stream of valid requests (such as the request to update the keyboard lights). A well known example of an undesirable KVM malfunction is a "crazy mouse" which was quite common with early KVM switches and was caused by data loss on PS/2 systems with the result that the mouse darted around the screen randomly clicking and opening windows. The unidirectional design of the AdderView Secure ensures that the influence of signalling on one port cannot flow past the data diodes. This means that overload signalling on one port will not affect the operation of another port. USB signalling is not susceptible to the failure mechanism that caused the crazy mouse on PS/2 systems. |
| Signalling by means of shorting the power supply or loading the power supply | Each port is independently powered by its USB port. Shorting the power supply on one port will not cause the power on other ports to be switched off. |
| Tampering with the switch | The switch is fitted with tamper protection measures. |
| Microprocessor malfunction or unanticipated software bugs causing data to flow between ports | Unidirectional data flow is enforced by hardware "data diodes" so data isolation doesn't rely on software integrity. |
|
Subversive snooping by means of detecting electromagnetic radiation emitted from the equipment |
Carefully shielded metal case with dual shielding in critical areas. |
|
Detection of signals on one computer by monitoring for crosstalk (leakage) signals on another computer |
No connection to sensitive analogue inputs (such as computer microphone ports) are provided. A very high level of crosstalk separation is provided between signals from different computers. |
|
Malicious modification of microprocessor software causing data to leak between ports |
Data isolation is assured by hardware and so is not compromised by any changes to the microprocessor software. Microprocessors use one time programmable memory so flash upgrades are not possible. Case uses counter-sunk screws which can be protected by tamper-evident seals. |
|
Buffered data within a keyboard or mouse is sent to the wrong computer after switchover |
Keyboard and mouse are powered down and reset between each switchover to ensure that all buffers are cleared out. |
| Data leakage by means of monitoring conducted emissions on mains power | The power circuitry provides strong protection against signal leakage via the power cable. |









